In my last blog, I briefly described how Enarx works to provide Confidentiality on deployed workload on the server-side.
Let's Zoom inside the Hardware Abstraction layer.
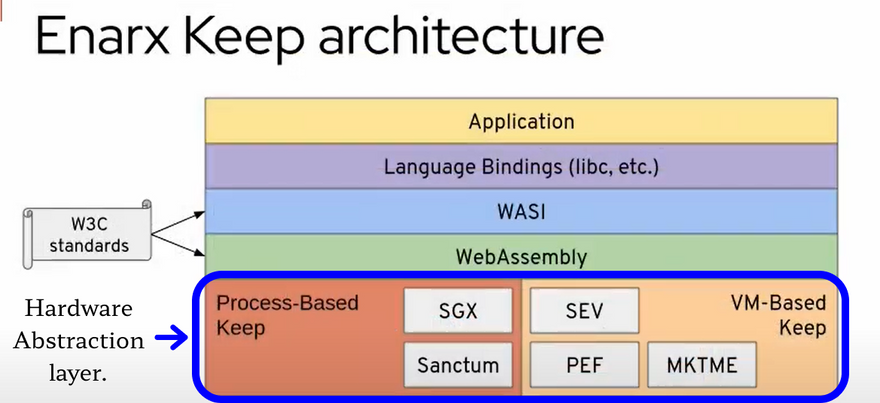
CPU splits the application into two parts The Untrusted part and the Trusted part that executed the wasm binary inside Enclave, which ensures that even a Privileged system code cannot access this data.
To secure the input parameters from getting observed and modified by the unsecure code The membrane between these two regions is defined extremely strictly towards calling the function from both ends.
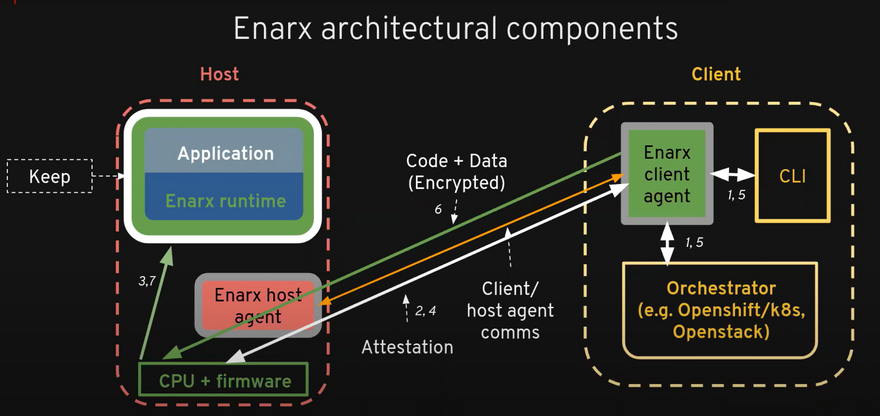
Let's come back to the same workflow I left you on, in the last blog.
For Confidentiality The Host must have a TEE, to be sure about the validity of TEE on the Cloud Host side the Chip manufacturer provides a cryptographic mechanism called Attestation.
Attestation
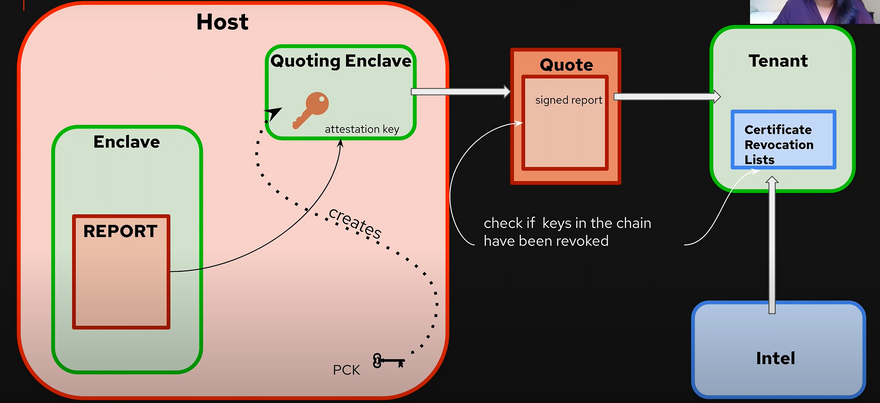
A report of the enclave is obtained by computing the secure hash over the inputs used to create the enclave. This allows the source party to verify the source enclave's identity.
In the case of Intel, it provides a Quoting Enclave that verifies the Report so generated by signing the report with a device-specific asymmetric attestation key. it is derived from the Provision Certification key one per CPU.
This whole process generates a Quote which is a signed report this is then sent to the tenant to verify whether the measurements are as expected or not, then the tenant verifies the integrity of the signature chain by the Certificate Revocation list providing the details of compromised keys if any published by CPU manufacture.
Now since the Tenant has verified the environment, then the wasm file gets encrypted inside the keep with a session key generated with every new keep.
Inside the keep, the data gets decrypted during the time data is processed since it has the key, and runs the file in its standard format.
image from https://youtu.be/JD70E7HHjlc
Let's try to relate this process with a real-life example out of the computer this time.
Illustration based explanation:
Consider Alice ya was about to deploy her workload to the cloud but before that was curious about the cloud scenario and wants to know the best practice one should follow while cloud computing for complete data confidentiality and integrity and she ended up with Enarx.
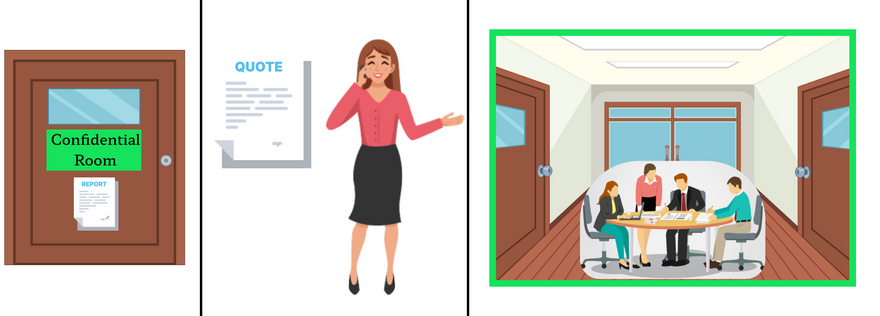
Suppose Alice has some Documentation work on her business and for that, the office staff asked to post her data to the postal address of office name Cloud but She decided to hire Enarx instead so that she can track her data and ensure its confidentiality.
Enarx is a middleman who serves clients with his extremely secure briefcase through which no one can escape the data unless they are authorized with a key to that briefcase everything inside the briefcase is written in such a language that any office staff can process but the biggest fact is the data is only accessible If you have valid accessibility proof and are certified authority.
It follows a very interesting technology named Zero-knowledge through which he can verify the verifier of the data is correct without even telling a percentage of knowledge about the data.
The next post will be based on ZKP and I'll demonstrate Demo based on the Enarx technique for confidential workload with ZKP.
Inside the office, he makes sure the office changes have created a separate trusted room for work processing and it is done with the generation of the report based on the measurement of input used to create the Room for confidential work. it's then sent to Alice and she verifies that everything went as expected.
Once she shows a green flag, Enarx then enters the room and discusses the process with the trusted Officers only and completes the documentation work for which he was assigned by Alice.
So just like Enarx works you can relate everything with the process involved in Enarx keep architecture.
The data inside brefcase locked with key as encrypted data, The Office with the Host Cloud, Confidential Room with Enclave, Report and Quote generation and verification with Attestation, Authorised officers as CPU, Firmware and Enarx it self as middleware.
Reference:
Strengthen Enclave Trust with Attestation
Enarx: protection for data in use - SGX: attestation & syscalls - Jyotsna Penumaka
From Zero to Hero: Making Confidential Computing Accessible by Nick Vidal | OC3 2022







Top comments (0)