In the previous blog post, we analysed the popularity/desirability of various programming languages for WebAssembly/WASI among wasmtime users. The Enarx project uses wasmtime as a runtime and, in principle, if an application works on wasmtime, then it should work equally well on Enarx.
Good support for WebAssembly/WASI for a given language unlocks a whole ecosystem and allows large developer communities to make use of WebAssembly (and Enarx). While it's still early days for WebAssembly on the server-side, we've observed communities from languages like Go/TinyGo, JavaScript, Java, Python, and C# investing on providing better support for WebAssembly/WASI.
The development of open standards and implementation of WASI (WebAssembly System Interface) is spearheaded by the Bytecode Alliance, a nonprofit organization that was founded in 2019 by Mozilla, Fastly, Intel, and Red Hat, with the endorsement from the W3C (World Wide Web Consortium). The CNCF (Cloud Native Computing Foundation) also plays an important role, as it hosts WebAssembly runtimes like WasmEdge and WasmCloud.
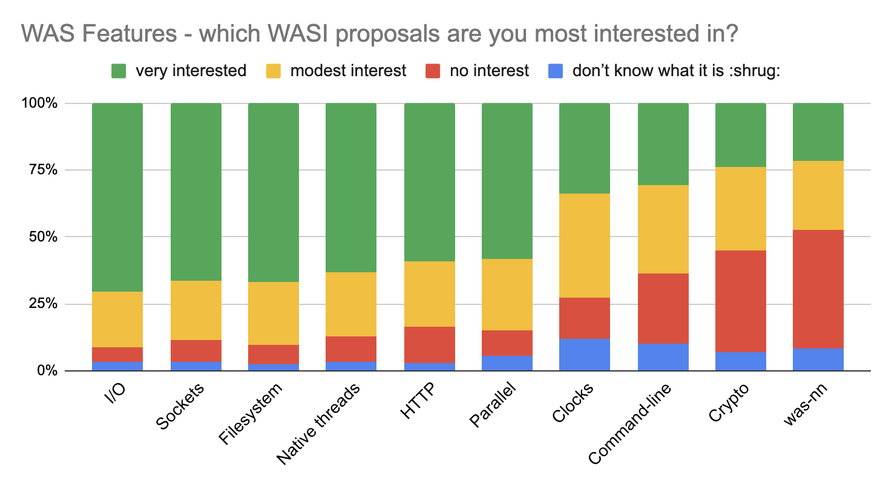
Currently there are several WASI proposals that are being developed. The State of WebAssembly survey provides a comprehensive overview of the existing WASI proposals and which ones the community are most interested in, as can be observed in the chart below. There is a lot of interest in I/O, sockets, filesystem, and threads:
The Enarx project in particular is investing in advancing WASI support in the Rust language, and we have contributed upstream to sockets, threads, and crypto.
We have contributed upstream with the implementation of sock_accept(), as well as with a Wasm server using the Rust mio and tokio frameworks. Nathaniel McCallum, co-founder of the Enarx project, has delivered a presentation about this contribution at Wasm Day Europe 2022.
We have also implemented WASI threads in wasmtime, which provides a mechanism for spawning threads, and we are currently developing some examples in Rust. These changes should get merged and land on an upcoming wasmtime release, but for serious threading/shared memory support a lot has to be done to the internals so that it's thread safe.
As for crypto, we have contributed to the wasi-crypto crate and we are pushing it to move to WIT as the specification format. We have also created a signing server in Rust which uses wasi-crypto to sign an arbitrary binary blob.
We are also continuously creating examples and demos and publishing them to Codex. These examples and demos are made available through Try Enarx, where users can easily launch these WebAssembly applications within TEEs (Trusted Execution Environments) directly from the browser with a click of a button.
In our WebAssembly Guide, developers can find information on how to get started using WebAssembly and Enarx using various languages, from Rust to Go. There are instructions on installing the necessary toolchains for each language as well as a common WebAssembly example (the Fibonacci sequence) across 14 programming languages.
Together with the WebAssembly community, we are publishing tutorials at Wasm.builders. The Enarx community has so far contributed with over 100 tutorials and articles and the Wasm.builders community has surpassed 1500 members.
Additionally, we are implementing a VS Code extension which will provide developers with a set of tools to help them learn, develop, test, and deploy WebAssembly applications to Enarx.
We have also created Drawbridge, a repository for WebAssembly applications, and we are working closely with the Bytecode Alliance as part of the WASI SIG Registries, with a special focus on security.
Finally, one of our key contributions and a core value proposition of Enarx is to render Confidential Computing accessible by making it possible for WebAssembly applications to be deployed within TEEs. We believe that Confidential Computing and WebAssembly are complementary technologies that have a huge potential to revolutionize security in the public cloud, on edge, and even on-premises.
If you are interested in learning more about Enarx and how we make use of WebAssembly, please check our website and join our chat.
This blog post is part 2 of WASI language support. Please check part 1 of the series.






Latest comments (0)