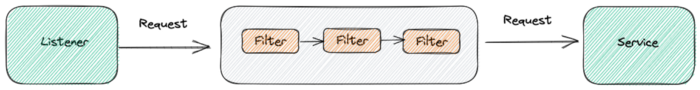
Envoy is an open source service proxy especially designed for cloud native applications. It has a wide variety of features like connection pooling, retry mechanism, TLS management, compression, health checking, fault injection, rate limiting, authorization etc. Those are achieved with built-in http filters. And today I will talk about a special filter which name is WASM Filter.
This article is not meant for explaining what is WASM, so I am skipping explaining WASM instead I will add resources for that at the end of the article.
Why We Use WASM Filter
In Trendyol Tech. We are using Istio as a service mesh. And our team’s (DevX) responsibility is improving developer experience by developing applications which meets common requirements of microservice’s like caching, authorization, rate limiting, cross cluster service discovery etc.
Since we already use Istio why not take advantages of the power of Envoy Proxy’s extensibility.
Our use case is acquiring JWT token for microservice’s which identifies that microservice application. When we want to avoid every team to write the same code in different languages, we can create a WASM Filter and inject it into Envoy Proxies.
Advantages of WASM Filters:
- It allows to write code in any language which has WASM support
- Dynamically load code to Envoy
- WASM code is isolated from Envoy so crashes in WASM not affect Envoy
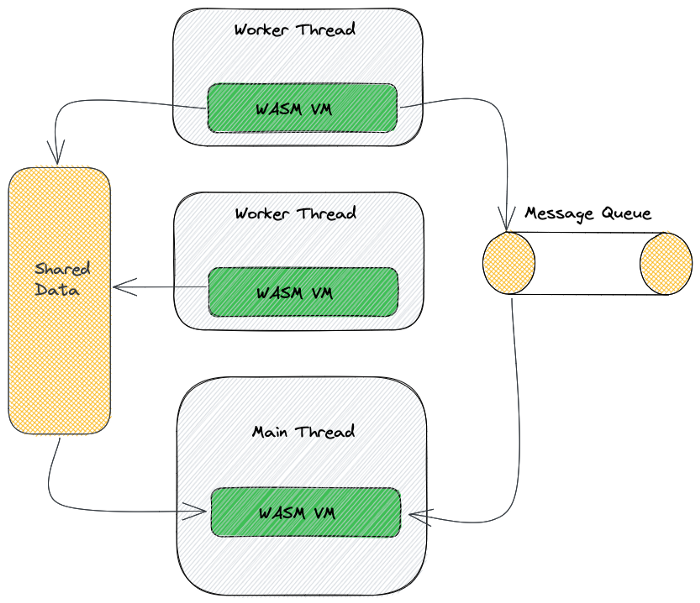
In Envoy Proxy there are worker threads that handles incoming requests. Every worker thread has its own WASM VM. So if you write time based operational code it works separately for every thread.
In Envoy Proxy every worker thread isolated from each other and has one or multiple WASM VM. There is also a concept called WASM Service for inter thread communications and data sharing (we are not cover this).
Writing WASM in Go
We are going to use tetratelabs/proxy-wasm-go-sdk to write WASM in Go. We also need TinyGo to build our Go code as WASM.
Our use case is very simple so we write a code which sends request to JWT Api for every 15 second. It extracts authorization header and sets it’s value to a global variable and puts that value to response header of every incoming request. We also set “hello from wasm” value to another header called “x-wasm-filter“.
In the OnTick function we are making http call to a service known by Envoy as cluster.
Let’s build our go code as WASM:
tinygo build -o optimized.wasm -scheduler=none -target=wasi ./main.go
Now we need to configure Envoy Proxy to use WASM Filter for incoming requests. We will define a routing rule and a WASM filter for our WASM code, also we define a cluster which represents our service.
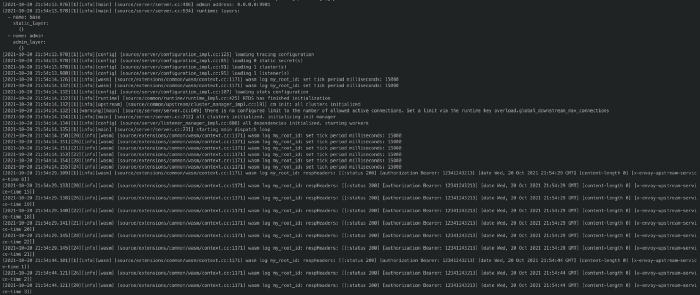
I put all of the files into same directory. Now let’s run Envoy Proxy in Docker:
docker run -it — rm -v "$PWD"/envoy.yaml:/etc/envoy/envoy.yaml -v "$PWD"/optimized.wasm:/etc/envoy/optimized.wasm -p 9901:9901 -p 10000:10000 envoyproxy/envoy:v1.17.0
As we can see from logs our WASM Filter started to work and sending request to JWT Api in every 15 secon
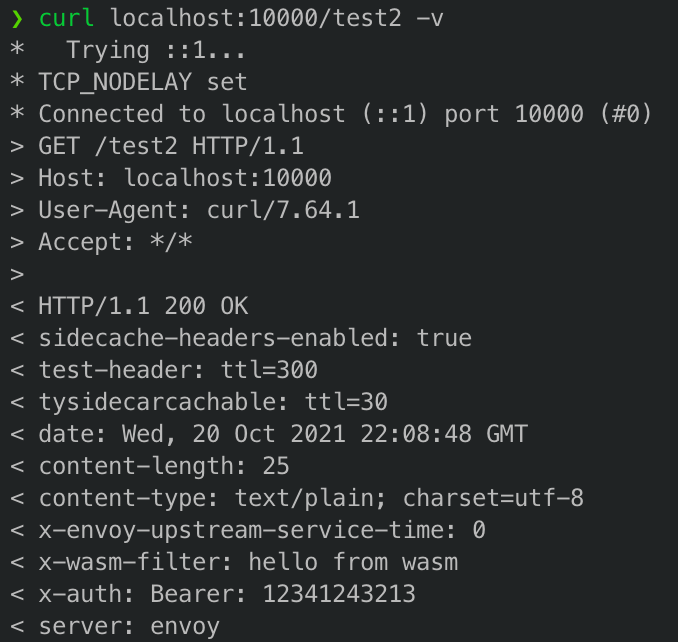
Now let’s send a request to Envoy Proxy. We configure Envoy to listen incoming requests from 1000 port and we start our container with port mapping. So we can send request to localhost:10000:
In the response headers we can see “x-wasm-filter: hello from wasm” and “x-auth” values.
Thank you for reading so far. I hope it will give you a perspective about how and why use WASM in Envoy Proxy.
You can see full example in github:
 mstrYoda
/
envoy-proxy-wasm-filter-golang
mstrYoda
/
envoy-proxy-wasm-filter-golang
A WASM Filter for Envoy Proxy written in Golang
envoy-proxy-wasm-filter-golang
A WASM Filter for Envoy Proxy written in Golang
Build
tinygo build -o optimized.wasm -scheduler=none -target=wasi ./main.go
Run Envoy Proxy in Docker with WASM Filter
docker run -it --rm -v "$PWD"/envoy.yaml:/etc/envoy/envoy.yaml -v "$PWD"/optimized.wasm:/etc/envoy/optimized.wasm -p 9901:9901 -p 10000:10000 envoyproxy/envoy:v1.17.0
Resources
 tetratelabs
/
proxy-wasm-go-sdk
tetratelabs
/
proxy-wasm-go-sdk
WebAssembly for Proxies (Go SDK)
This project is in its early stage, and the API is likely to change and not stable.
WebAssembly for Proxies (Go SDK) 

The Go SDK for Proxy-Wasm, enabling developers to write Proxy-Wasm plugins in Go This SDK is powered by TinyGo and does not support the official Go compiler.
Getting Started
- examples directory contains the example codes on top of this SDK.
- OVERVIEW.md the overview of Proxy-Wasm, the API of this SDK, and the things you should know when writing plugins.
Requirements
- Go 1.17 or higher.
- TinyGo - This SDK depends on TinyGo and leverages its WASI (WebAssembly System Interface) target. Please follow the official instruction here for installing TinyGo.
- Envoy - To run compiled examples, you need to have Envoy binary. We recommend using func-e as the easiest way to get started with Envoy. Alternatively, you can follow the official instruction.
Installation
go get cannot be used…








Top comments (0)