In a world where everyone is trying to fetch your data in any way possible either to sell you their services or to have malicious access to perform nasty, you cannot have faith or trust in vendors processing your data while computing, this further amplifies with multiple layers of hands keeping a record of data.
In this blog, I will try to impart light on the solution Enarx provides as a Runtime to the users practicing cloud computing. It respects your data integrity and confidentiality. the whole ideology behind will have you on a rollercoaster ride with tons of new terminologies/technology if you too an abecedarian and are curious about cyber security. so stay tuned with me, we'll end up with so much out of it for sure.
Contents in this Series:
- TEE (Trusted Execution Environment)
- Standard Cloud Virtualisation
- ENARX project
- ZKP (Zero-knowledge proof)
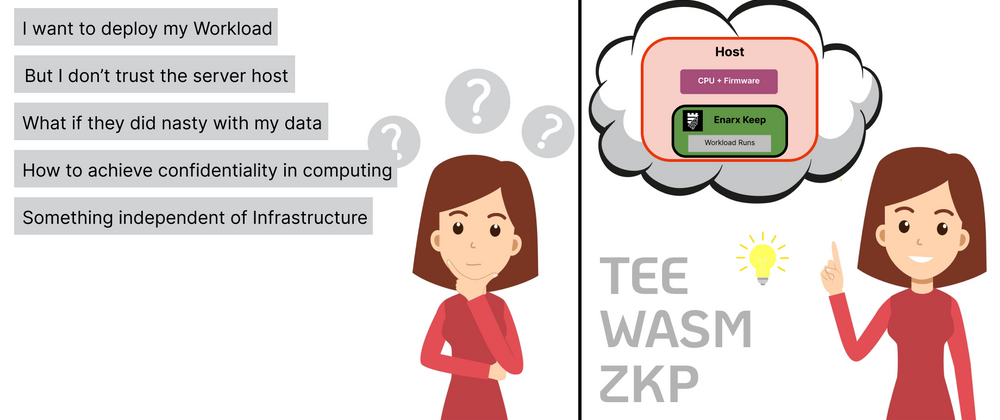
Meet Alice she is currently working on a workload in the server, she wants to deploy/host her work on the internet. but before doing so she wants to be sure about the environment towards confidentiality.
To understand these will first need to learn data processing before.
There are three data states:
- Data in transit: moving from one location to another across the internet.
- Data at rest: stagnant inside your system memory.
- Data in use: data being processed, updated, erased, accessed, or read by a system.
In the private cloud or the public cloud, cryptography has been seen as an emerging solution to protect data in all states. encryption safeguards both data in transit and data at rest,
but for data in use you need to have an extra edge over the protection layer because this type of data gets accessed by multiple users and thereby exposed enough for malicious activity, lets's zoom in a bit more inside.
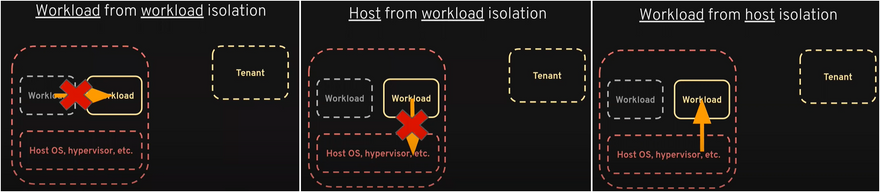
To retain confidentiality and integrity of data and to achieve that one needs to check complete Isolation which can be divided into three parts:
Workload to workload isolation ( Temporal isolation among virtual machines ): while cloud computing with virtualized data limits the temporal and interferences between multiple VMs despite the fact they are running on the same physical host and sharing a set of physical resources such as processors, memory, and disks.
Host from Workload Isolation: To limit the interference between the workload and the host operating system, hypervisors, etc. so that we can ensure no nasty can be done by any compromised or malicious workload if any.
Workload from the Host Isolation: so that the host cannot crash through the line of demarcation and see whatever is inside the workload this is the security piece and it's incredibly important.
The current scenario:
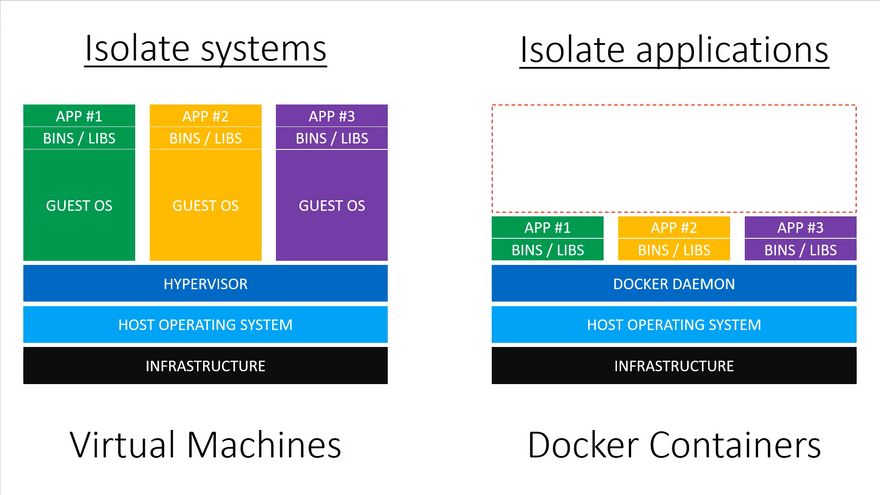
We have Containers with Cgroups provide metering and limiting, VMs, Hypervisors, Seccomp (Secure computing mode) allows the process to make the one-way transition into a secure state where it cannot make any system calls except exit, SE Linux (Security-Enhanced Linux) allows admin to have more control over who can access the system, and are working excellently to provide the isolation in first two cases.
Image from: https://youtu.be/TvnZTi_gaNc
For Workload from Host Isolation these standard techniques lack behind since the host is in charge of mapping memory pages to the workload thereby can look into your data with standard protocols.
Alice is concerned regarding the integrity and confidentiality of her sensitive data. as she is now aware of the fact that.
Then is there a way we can prevent modification or unauthorized access to data?
yus... this is where TEE comes into play.
TEE (Trusted Execution Environment)
They are chip-level hardware-based security instructions. a secure area of the main processor provided by CPU manufacturers called Enclaves. can be used on-premises, in the cloud, or within embedded hardware platforms.
In the private cloud or the public cloud, cryptography is considered as best practice to protect data in all states.
TEE comes with a certified hardware crypto engine for key management and encryption. keeps your data encrypted except when it's actually being processed by the chip.
CPUs providing TEE: Intel SGX, AMD SEV, RISCV’s Sanctum, and many more.
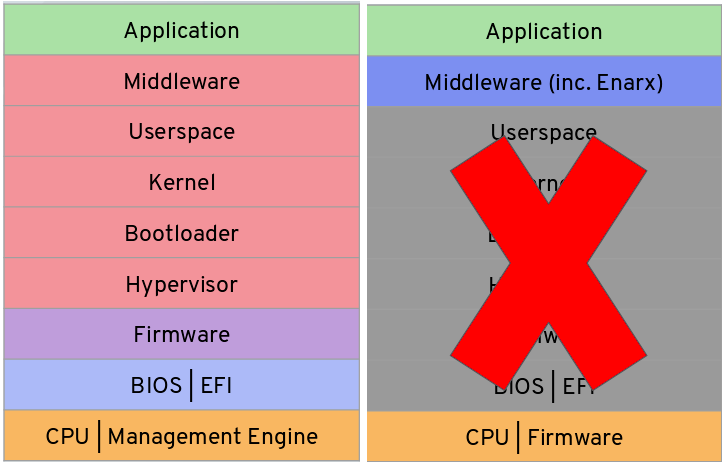
There are multiple layers your data go through in order to virtualize and process your data. Let's Understand them.
Standard Cloud Virtualisation Architecture
Each color represents different vendors with admin rights enabling them to sneak into your data. in order to reduce Data breaching and simplify data management.
CPU isolates sensitive code inside TEE, cutting down these layers to many folds and blocking their access to TEE thereby preventing data from the rest of the part. leaving Application, middleware, and CPU itself for data processing.
There are many Benefits of TEE you can check the link.
But it has some major Drawbacks too
No Portable Attestation and Development: For fundamentally different infrastructure we need to specifically rewrite the whole application. and thereby have to go through different Attestation models w.r.t machine because TEE are not capable of switching platforms.
Limited SDK support: Restricted language availability.
This means you cannot deploy your work to an AMD device if it's developed in Intel-based Infrastructure. along with the language barrier, so one needs to be aware of that too, this complicates the whole process.
and thereby are not the true solution to the problem and to Overcome these we have ENARX
ENARX
A part of Condidential Computing Consortium from Linux Foundation.
WebAssembly + Confidential Computing
Enarx provides you Confidential Computing based on Trusted Execution Environments(TEEs) and hardware encryption technology, and has portable support over multiple platforms and many languages.
so you can now deploy your workload with ENARX Runtime without being worried about machine Infrastructure and language SDK.
thereby caters to deployment and development much easier, and fast, Language and Architecture Independent.
So now you *don't have to *
- Rewrite the application for particular platforms or SDKs.
- Attestation and deployment Enarx do that for you.
Let's have a look at its meaningful logo
Castel + shield + Chip level instruction.
In Enarx keep the work keep is derived from the room that was 2.5 meters thick inside the castle. thereby were considered as safest place
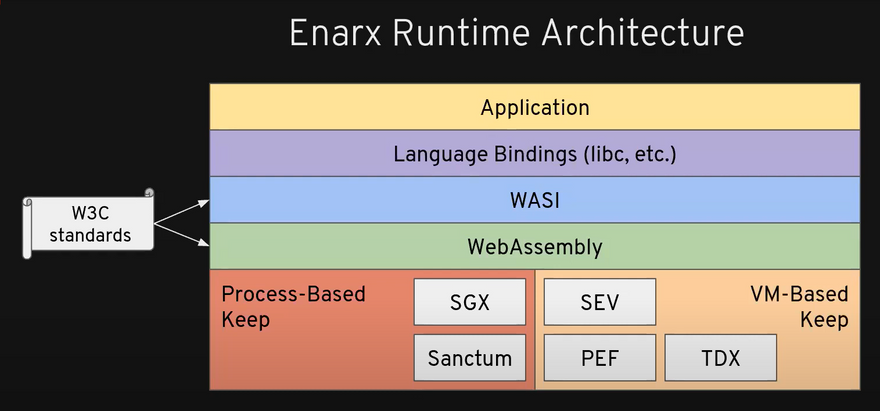
How Enarx manages to do that ?
Application: The application or workload you wrote and trusted at the same time.
-
Language Bindings (libs, etc.): Library wrappers consist of a thin layer of code(Shim).
- refines a poorly designed or complicated interface.
- Allow code to work together due to incompatible data formats
- Enable cross-language and/or runtime interoperability.
WASI(WebAssembly standard Interface): it allows WebAssembly out of the browser that is on the server-side.
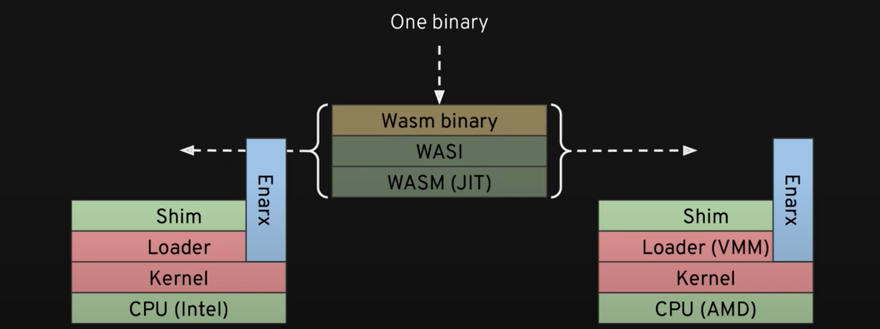
WebAssembly: is a portable runtime compilation target that supports 40+ languages to date and has bought them to web browsers. thereby enabling Enarx to run the same binary on different TEE.
I have written a lot on WebAssembly on my blog: WebAssembly: New Capability to Web you can have a look on it.
- Hardware Abstraction Layer: Currently Enarx supports two different major approaches to enable and lets you run your workload in the same binary and different TEEs.
Process based TEE: Intel Software Guard Extensions(SGX), RISCV's Sanctum
VM based TEE: AMD's Secure Encrypted Virtualization (SEV), Intel's Trust Domain Extensions(TDX), POWER's Protected Execution Facility(PEF).
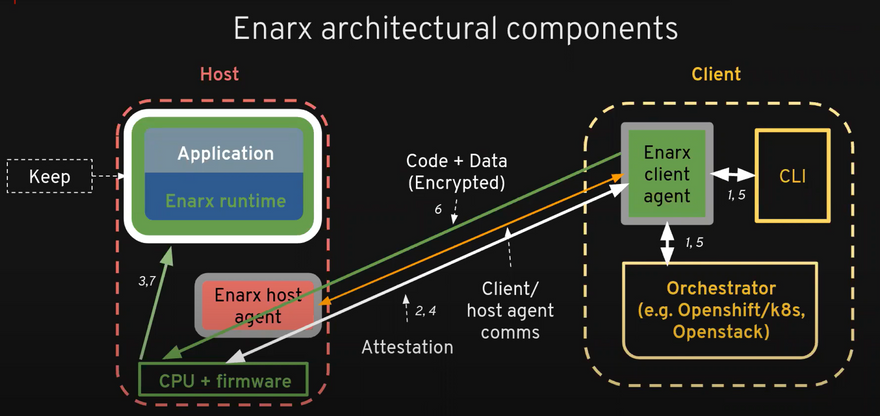
Enarx keeps: is a hardware isolated environment using technologies such as Intel SGX or AMD SEV.
On the client side Through Command line Interface(CLI) we send instruction to Enarx client agent on that later sends the encrypted Data + code to the server which then with CPU and Firmware creates a Keep in the Host and pushes your data inside.
It sends a report back to the Tenant so that it can verifiy every this is going as expected. this process is called Attestation.
In the next part of the series I will write a more elaborated version of Enarx architectural componet and its working.
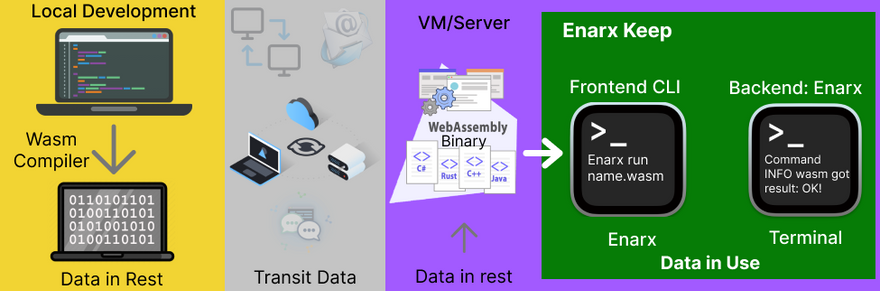
This is a workflow of what image I could have build yet of now
Inspired by Enarx demo by @ajay272191 and @jennifer .
Enarx uses a very interesting method called Zero-knowledge proof as its core technique in order to keep your data safe by proving the verifier without even disclosing a single bit of it.
We will discuss that in further blogs
Summary:
We learned What TEE is, How Enarx with webAssembly creates a portable Runtime independent of Machine architecture giving us a wide range of SDKs to write the application on.
References:
Virtual Machines vs Docker Containers
Enarx official Website
Enarx by Mike Bursell (Red Hat) | OC3 2021
What is a trusted execution environment (TEE) and how can it improve the safety of your data?
Enarx 2020 demo
A Technical Introduction to Enarx







Top comments (0)