It's good to be back with another interesting blog!
WASM is considered as the third generation of Cloud Computing, and it is expected to boom in the upcoming time therefore Data Security needs an upgrade to keep up.
In previous blogs, we explored the properties & applications of WebAssembly,
But today we're going to learn about CCC (Confidential Computing Consortium) is an open-source community powered by The Linux Foundation, which works as the icing on the cake for Wasm.
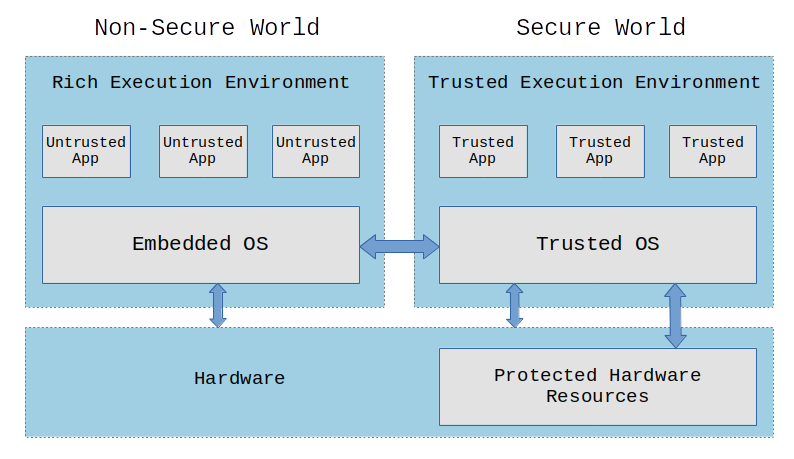
Confidential Computing protects data in use by performing the computation in a hardware-based Trusted Execution Environment. These secure and isolated environments prevent unauthorized access or modification of applications and data while in use, thereby increasing the security assurances for organizations that manage sensitive and regulated data.
Importantly, the definition is not limited to “cloud” uses, but can be applied anywhere including public cloud servers, on-premises servers, gateways, IoT devices, Edge deployments, user devices, etc. It is also not limited to such trusted execution being done by any particular processor, since trusted processing might also be in various other places such as a GPU or a network interface card. Neither is it limited to solutions that use encryption, though this is the most common technique employed.
Trusted Execution Environments (TEEs):
A Trusted Execution Environment (TEE) is defined by the CCC, following common industry practice, as an environment that provides a level of assurance of the following three properties:
a. Data confidentiality: Unauthorized entities cannot view data while it is in use within the TEE.
b. Data integrity: Unauthorized entities cannot add, remove, or alter data while it is in use within the TEE.
c. Code integrity: Unauthorized entities cannot add, remove, or alter code executing in the TEE.
In the context of confidential computing, unauthorized entities could include other applications on the host, the host operating system and hypervisor, system administrators, service providers, and the infrastructure owner—or anyone else with physical access to the hardware.
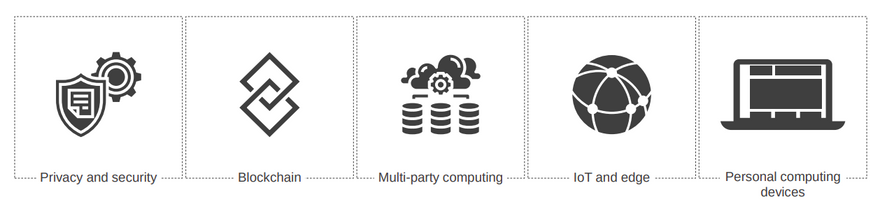
Technologies that will be benefited by CC:
There are several projects within CCC with the main focus on the security and privacy of digital data. They are as follows:
- Enarx
- Gramine
- Keystone
- Occlum
- Open Enclave SDK
- Veracruz
Organisations that are part of this initiative:
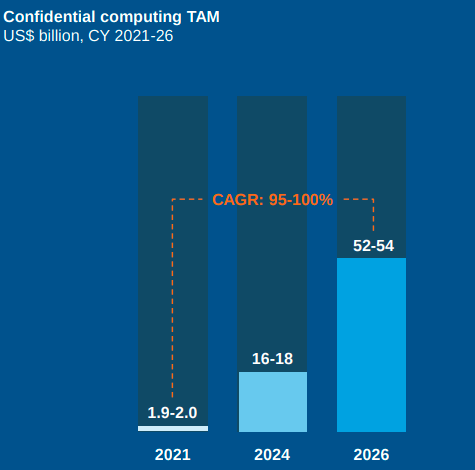
Overall Expected Market growth of Confidential Computing:
In a report generated by the Everest group, it is expected about CCC is
- The Total Addressable Market (TAM) for CC is likely to grow at least 26x over the next five years in the best-case scenario due to growing enterprise awareness of confidential computing.
- The CC hardware and software markets are poised for exponential growth backed by expanding regulations, demand for comprehensive security postures, and an appetite for new revenue generators.
- Multi-party computing and security-specific use cases across industries will be the biggest growth drivers for the technology.
Conclusion:
As a result, due to the increasing complexity of technology, privacy and security have become more difficult to protect. The Confidential Computing Consortium is a great initiative that is working to keep data secure in any system by creating a sophisticated enviornment. Getting more and more contributors in will put this on a meteoric rise within a short time.
Keep an eye out for the next blog in this series in which we will learn about the various projects that make up the Confidential Computing Consortium.
References:
- https://confidentialcomputing.io/
- https://confidentialcomputing.io/wp-content/uploads/sites/85/2021/10/Everest_Group_-_Confidential_Computing_-_The_Next_Frontier_in_Data_Security_-_2021-10-19.pdf
- https://confidentialcomputing.io/scope/
- https://www.trustonic.com/technical-articles/what-is-a-trusted-execution-environment-tee/
- https://embeddedbits.org/introduction-to-trusted-execution-environment-tee-arm-trustzone/
Do comment your thoughts and suggestions related to the blog and please share if you found it useful.








Oldest comments (0)